Blog
What is SIEM and what’s its benefits ? SIEM (Security Information and Event Management) is a hybrid of Security Information Management (SIM) and Security Event Management (SEM). A SIEM system analyzes security warnings issued by apps and networks in real time. SIM is the gathering, monitoring, and analysis of security-related data, such as log files, […]
Lets discover Elasticsearch for APM works Have you ever wondered how to simply monitor your application’s performance? Elastic APM is the solution. Elastic Application Performance Management (APM) is a new Elasticsearch 6.1 functionality (in beta and alpha in 6.0). Opbeat (an application performance monitoring – APM – firm) merged with Elastic a few months […]
Outsourcing facility management is a difficult step for most facility managers. Outsourcing facility management has the potential to save your organization money if done right, it also has the potential to harm your ROI if you outsource the wrong task to the wrong outside vendor at the wrong time. Facilities management can account for […]
What Is Security Information and Event Management (SIEM)? Security information and event management (SIEM) is a cybersecurity system that gives you a unified, simplified view of your data, understanding of security activities, and operational capabilities so you can detect, look into, and address security risks efficiently. That combines security event management (SEM) and security information […]
Any company must place a high priority on safeguarding client data from internet threats. Simply installing the most latest antivirus software protected your company from these threats. Businesses need additional protection to combat these dangers, which is why IT security is a field that is always changing. Endpoint detection and response (EDR) can more effectively […]
The most terrifying words for any IT leader to hear are “zero-day exploit” which refers to a cyber attack that targets a software weakness. Once the software vulnerability is identified, the attacker immediately develops an exploit and launches an attack using it. Organizations must therefore take precautions to protect themselves from dangerous vulnerabilities and must […]
The new Amazon EKS Anywhere is a deployment option, users may now build and manage Kubernetes clusters on their own, AWS-supported infrastructure. Customers are able now to use VMware/bare metal deployments to operate Amazon EKS Anywhere on their own on-premises infrastructure. In addition to offering tools for automating cluster administration, Amazon EKS Anywhere, a […]
What is Monitoring CISCO SWITCH? Would you like to know more about how to monitor Cisco switches using Zabbix? You are in the right place, but 1st let’s get to know more about this CISCO Switch, what it is, and then how to monitor it with this open-source software Zabbix. CISCO Switch Switch are essential components […]
Modern firewalls are purpose-built to defend against ransomware – but to do so, they need to be given the opportunity to do their job. As ransomware attacks become more targeted, tailored, and stealthy, capable of causing havoc to organizations and their networks, applying best practices to get the most out of your firewall is pivotal. […]
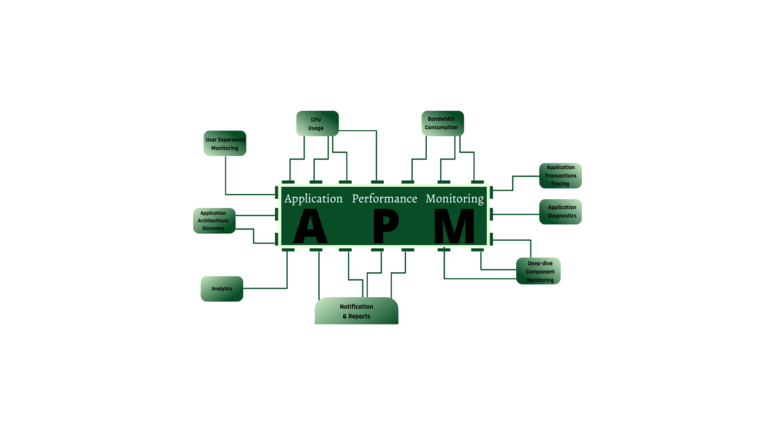
Application Performance Monitoring, what are you talking about? Application Performance Monitoring is a set of tools and procedures that enable IT workers to ensure that the applications consumers use satisfy performance standards and deliver a positive user experience. APM ensures that services deliver to customers at the desired level and detects errors and anomalies with […]
Data Driven? What are you talking about? Data Driven is making data and analytics a core component of your business strategy, organizational culture, and processes . It doesn’t involve installing applications and tools in fact hiring a dedicated team of data professionals, committing to a significant data infrastructure investment, and aslo running a one-time data […]
FortiGate is one of the most popular NGFW (Next-Generation Firewalls). This project’s primary purpose is to create an open-source log monitoring platform dedicated to FortiGate based on this firewall’s logs. It is based on ELK, which stands for Elasticsearch, Logstash, and Kibana. This should be considered a free alternative to Forti Analyzer from a functional […]
5G is the next generation of cellular technology that will revolutionize using the internet. 5G will be quicker than 4G and more reliable and efficient. Enterprises are resorting to the private 5G network, a private local area network (LAN) constructed using 5G cellular technology and edge device connectivity, to address increased network traffic demand and […]
Why001 is IT Monitoring and Reporting Critical to the Success of Your Company? Network monitoring is a critical IT activity that provides numerous benefits to businesses of all sizes. It can help you save money on network performance, staff productivity, and infrastructure expenditures, and it is a lot more strategic than its name suggests. It […]
Due to the continuous growth of software in the technology sector, development teams are constantly under pressure to satisfy rising customer expectations for business applications. The following are common expectations: Performance enhancement Adding new features Ensured uptime and availability The traditional software development process has evolved with the rise of cloud-based applications. Rather than […]
Kubernetes handles many of the difficulties with software-based 5G telecom networks. Telecom operator’s usage of Kubernetes to build highly automated, multi-environment infrastructure with various network interfaces will dictate how 5G services are provided. In the form of a cloud-native application, 5G also allows previously inconceivable data transmission speeds and high-performance remote computing capabilities. In terms […]
Because your database is one of the most significant aspects of your company, selecting the correct cloud provider and transferring your databases to the cloud is crucial. Migrating your organization to the cloud makes it easier to administer and use the cloud’s advantages. Amazon Relational Database Service (Amazon RDS) is an Amazon Web Services […]
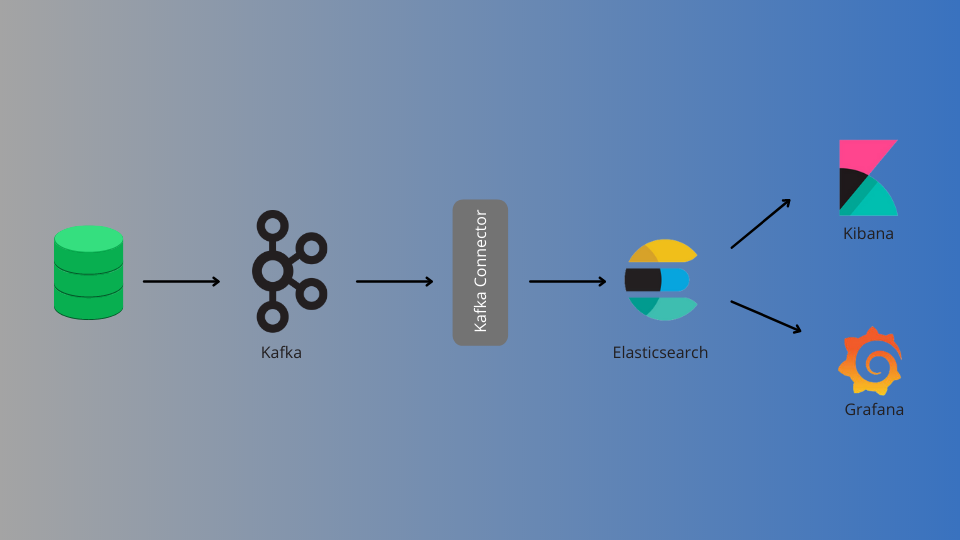
In today’s digital world, real-time data analytics and business intelligence insights are becoming increasingly prevalent. Real-time data analytics aids in making timely and relevant judgments. We’ll see why Kafka is utilized for real-time streaming data analytics in this blog post. What is Kafka? Kafka is open-source software that allows you to store, read, and […]
Having a Telecoms Noc Outsourced The dreaded d-word… downtime! is the most significant pain point for everyone who controls a communications network. Working with a professional network operations center (NOC) partner to monitor your network is necessary. When properly managed, these centers enable you to be proactive and respond to anticipated problems before they occur. […]
Telecom companies must keep up with new technological breakthroughs, stay competitive in one of the world’s most competitive industries, and comply with a slew of regulations. The role of data analytics in telecom is to give companies the simplest way to extract insights from all of their data. will generate more earnings by using a […]
Before you sign up for NOC services, here are some questions to consider Who is in charge of the NOC and where is it located? Always double-check the location details while signing up for a NOC Services. It is now normal practice among service providers in the market to withhold the geographical location of […]
Downtime costs $5,600 p/minute, which adds up to well over $300K p/hour Every organization is concerned with cutting costs, but the true cost of network outages is often overlooked. The overall cost of lost productivity lost revenue, and intangible costs associated with network outage is the cost of network downtime. Consider how much it […]
Modern and effective data analytics are essential for digital business success. Taking the first steps toward integrating data literacy into the business can be scary. Even if firms are beginning to recognize the financial benefits of data and analytics. Organizations that fail to properly exploit data assets, on the other hand, will fall behind. […]
Learn how to safeguard your company from hackers and how to prevent bad actors from causing damage if they gain access to your network. Your business handles sensitive data, as do all businesses. Keeping your data secure is a primary priority, whether it’s your customer’s personal information, your company’s financial records and accounts, or that […]
If you want to be a successful IT leader, you must cultivate a set of characteristics that will benefit both you and others around you. Industry executives and career gurus weigh in on what […]
The implementation phases of the APM app based on Kubernetes This second part deals with the design and implementation phase of the solution based on Kubernetes and its details. We’ll see how the Deployment of an APM on Kubernetes works in another way we’ll look at how to instrument a Go program so that […]
A major vulnerability in the popular Java Log4j logging package, called Log4Shell, discover on December 9, 2021. CVE-2021-44228 is a remote code execution vulnerability with a severity of 10 (the highest possible risk level) that allows an attacker to take total control of any compromised machine. What is log4j? The Apache Foundation has created […]
What is Kubernetes monitoring and the most open source tools used ? This article shows how the deployment of an Application Performance Monitoring (APM) solution for a Kubernetes -based application works to detect and fix issues related to that application. The notion of continuous deployment in the DevOps technique is of particular significance to this […]
Understanding and implementing security software may be difficult. This may make it more difficult to utilize and install secure designs. WireGuard software, on the other hand, strives to bring us together with security solutions. Its goal is to provide a robust VPN connection between two PCs with only a few setup options. Indeed, its […]
Automation tools are one technology that has had a transformative impact on system administrators. We may mention Chef or Puppet as tools. But for a long time, Ansible was the tool that won the tool fight automation. But, exactly, what is Ansible? The administrator should get familiar with the Ansible control environment after learning […]
Let’s take a look on what a Ticketing System is: An effective ticketing system is required to respond quickly and efficiently to users’ IT support requests. Tickets, which are frequently included in professional help desk software, allow users to request assistance while documenting an IT incident as well. The computer card thus created is […]
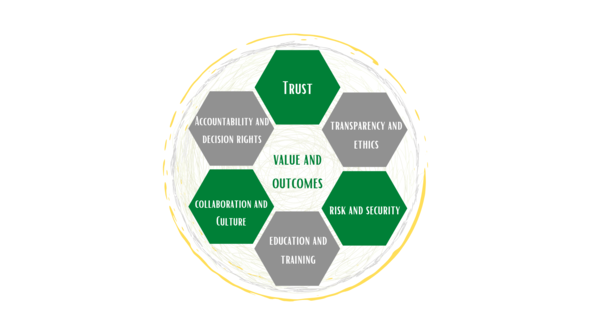
7 Key Foundations of Modern Data and Analytics Gouvernance This article will cover the 7 Key Foundations of Modern Data and Analytics Gouvernance, Facts or figures and information stored in or utilized by a computer are called “data.” They are facts that can be evaluated or used to learn more or make better decisions. The […]
To remain competitive in the quickly evolving business world of today, the capacity to manage change is crucial. Change management, which entails monitoring the recording, evaluation, authorisation, prioritization, planning, testing, implementation, documentation, and review of changes, is one strategy for bringing about change at various levels of an organization. A procedure inside the ITIL […]
Having these three tools and methodologies on hand will help you avoid system breakdowns in the future: Ticketing, ITIL and, Change Management. Facebook services such as Instagram, WhatsApp, Messenger, and the social network itself were affected by the global blackout. After a 6-hour outage, social networks and messages are back online. the internet giant’s […]
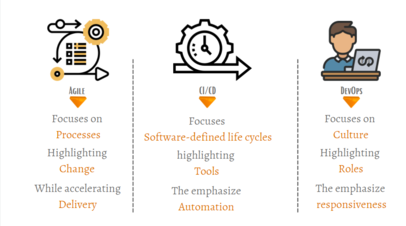
Agile, CI/CD, and DevOps are three of the most used terms in software development and testing circles. to understand the difference, it is best to start with what these terms actually mean. In this blog, we will be trying to uncover some of the major differences. · What is CI/CD?· What is Agile?· What is DevOps?· Differences […]
With the help of data, companies are able to make informed decisions which can have a significant impact on their business. Companies should invest in data-driven solutions that will help them gain insights into their business. Or hire experts who can provide actionable insights to the organization. Actionable insights for your business with data-driven Many […]
Internet of Things (IoT) is the new information technology (IT) that is drastically changing the way we do business. However, the impact of Internet of things in the manufacturing sector has yet been fully explored. Indeed, IoT is one of the main reasons behind the Industry 4.0 movement, as it will permit, data analytics and […]
Whether your data is stored in the cloud or on-premise, automation and orchestration make complex business processes run smoothly DevOps teams want to work quickly and you want to ship quicker, but most companies want to develop tools that allow sharing between teams and acquire a knowledge of scale. This is where automation and orchestration […]
Proactive monitoring and alert management can identify any potential issues before they become a problem and intervene to resolve them. Proactive management of alerts helps businesses to save time and money, by informing of all alerts and helping to avoid losing useful information inside the huge amount of information Today, more and more companies […]
With data analytics, you can get an understanding of what your customers want and need. You can also identify patterns in customer behavior, predict customer behavior and find patterns for new products and services. Data analytics is a process that allows you to extract insights from data sets that could otherwise be either too big or […]
- 1
- 2